CYBERSECURITY SERVICES
Our Team of Network and Security Engineers Understand Both the Technical and Regulatory Sides of Cybersecurity
Cybersecurity Practice Overview:
All 7 Layer Cybersecurity services are led by CISSP certified professionals.
7 Layer provides advisory and implementation services along with process and policy controls to protect against modern-day Cyber threats in the following three service areas

Our point-in-time security assessment leverages a risk-based approach to examine and enhance defense mechanisms against cyber-attacks. The assement helps identify threats that could affect the availability and reliability of systems and network infrastructure.
- Network and Systems Infrastructure
- Policy and Procedures
- Cyber Maturity Scope
- Remediation Roadmap
- Identify scope of Health check with Technology and Business leaders
- Coordinate access to the environment
- Schedule remote and onsite visits
- Vulnerability Scan
- Dark Web Scan
- Physical Security
- Inventory and control of assets
- Hardware Configuration
- Email/O365 Audit
- A/V Configuration
- DR and Back Up Analysis
- Data Protection
- Review identified vulnerabilities and risks
- Provide mitagation plan with timeline and associated cost estimates
- Cybersecurity scorecard and comparision with peers
Security Risk Remediation
- Configuration and process optimization
- Tools review/Optimization
- System/Software implementation
- Vulnerability Management/Penetration Testing
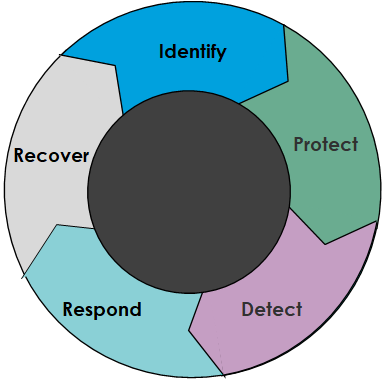
- Conduct health check on existing environment to identify current security posture and build a remediation roadmap
- Build Business Continuity / Disaster Recovery Plan to increase recovery speed and reduce data loss
- Implement remediation roadmap and optimize existing solutions to strengthen protection against modern-day threats
- Implement best practices Incident Response processes to reduce resolution time
- Deploy tools and processes to reduce detection time and impact to the business
- Security Program Development
- Security Standards
- Cyber Best Practice Tools, Policies and Training
- Reporting and Incident Tracking
- Regulatory and Compliance
Our fractional CISO services provide:
- Leadership, strategy and guidance in managing you organizations security risk
- Serve as a security advisor to senior management and Board of Directors
- Develop and assist in implementing Cyber/IT Security control Framework
- Develop IT security roadmaps and budgets in context of industry-applicable compliance, requirements and best practices
- Develop IT security risk management programs, including policy, procedures, and checklists
- Update IT security, incident response, and third-party management policy and procedures
- Provide checks and balances with in-house IT or security staff
- Guide remediation of security gaps and incidents
- Security Health Check
-
Our point-in-time security assessment leverages a risk-based approach to examine and enhance defense mechanisms against cyber-attacks. The assement helps identify threats that could affect the availability and reliability of systems and network infrastructure.
- Network and Systems Infrastructure
- Policy and Procedures
- Cyber Maturity Scope
- Remediation Roadmap
- Identify scope of Health check with Technology and Business leaders
- Coordinate access to the environment
- Schedule remote and onsite visits
- Vulnerability Scan
- Dark Web Scan
- Physical Security
- Inventory and control of assets
- Hardware Configuration
- Email/O365 Audit
- A/V Configuration
- DR and Back Up Analysis
- Data Protection
- Review identified vulnerabilities and risks
- Provide mitagation plan with timeline and associated cost estimates
- Cybersecurity scorecard and comparision with peers
- Security Risk Remediation
-
Security Risk Remediation
- Configuration and process optimization
- Tools review/Optimization
- System/Software implementation
- Vulnerability Management/Penetration Testing
- Conduct health check on existing environment to identify current security posture and build a remediation roadmap
- Build Business Continuity / Disaster Recovery Plan to increase recovery speed and reduce data loss
- Implement remediation roadmap and optimize existing solutions to strengthen protection against modern-day threats
- Implement best practices Incident Response processes to reduce resolution time
- Deploy tools and processes to reduce detection time and impact to the business

- Fractional CISO
-
Fractional CISOImplementing or enhancing your information security management framework can be a grueling task. 7 Layer Solutions will provide seasoned CISO leadership to aid you in building an effective program.
- Security Program Development
- Security Standards
- Cyber Best Practice Tools, Policies and Training
- Reporting and Incident Tracking
- Regulatory and Compliance
Our fractional CISO services provide:
- Leadership, strategy and guidance in managing you organizations security risk
- Serve as a security advisor to senior management and Board of Directors
- Develop and assist in implementing Cyber/IT Security control Framework
- Develop IT security roadmaps and budgets in context of industry-applicable compliance, requirements and best practices
- Develop IT security risk management programs, including policy, procedures, and checklists
- Update IT security, incident response, and third-party management policy and procedures
- Provide checks and balances with in-house IT or security staff
- Guide remediation of security gaps and incidents